
Cryptography for Everybody 3 years ago
cryptology, #cryptography, #cryptanalysis In this video, you learn about (classical) cipher type detection with deep learning and ...

Cipher ID 5 years ago

Franky Passive Income 3 months ago
hamster kombat daily cipher code today 12 July . cipher code today 12 july cipher codes to solve cipher today cipher code ...

Chomiks Explained 2 years ago
Cipher and Encrypted Chomiks are generally a really easy chomik with a hard to get realm, you can use a cipher identifier to get ...

Franky Passive Income 3 months ago
hamster kombat daily cipher code today 11 July . cipher code today 11 july cipher code key cipher today cipher codes to solve ...

Cikgu Atie 4 years ago
ceaser cipher & pigpen cipher.

Sevuhl sevuhl 4 years ago
Crack a few cipher's, SSH your way into the box and find you way over the wall to root! This room focuses on helping Nicholas ...

Shary Information 2 months ago
Assalamualaikum Everyone ♥️ ✓ Join Hamster Mining ✓ https://t.me/Hamster_kombat_bot/start?startapp=kentId6208575635 ...

Shary Information 2 months ago
Assalamualaikum Everyone ♥️ ✓ Join Hamster Mining ✓ https://t.me/Hamster_kombat_bot/start?startapp=kentId6208575635 ...

Crypto Diffusion 4 months ago
Je vous montre dans cette vidéo comment trouver par vous-mêmes le code DAILY CIPHER au quotidien afin de recevoir ...

Don't Panic Geocacher 3 years ago
This episode is part of a series that gives you some guidelines on how to solve mystery geocaching puzzles. The episode talks ...

Shary Information 2 months ago
Assalamualaikum Everyone ♥️ ✓ Join Hamster Mining ✓ https://t.me/Hamster_kombat_bot/start?startapp=kentId6208575635 ...

Shary Information 2 months ago
Assalamualaikum Everyone ♥️ ✓ Join Hamster Mining ✓ https://t.me/Hamster_kombat_bot/start?startapp=kentId6208575635 ...

Don't Panic Geocacher A year ago
In this episode, we are exploring the wonderful world of text based codes and ciphers that are frequently used in Geocaching ...

reyanimates 21 days ago
This whole theory type video might be a one time thing but we'll see ;) ———————————————————— Go Sub To ...

Almond Force 2 years ago
In this T3N4CI0US CTF 2022 video, we do a writeup of the french crypto challenge.

Andrii Sukhetskyi 5 months ago
Explore the cryptographic chronicles from the time of the Roman general Julius Caesar to the Advanced Encryption Standard ...

UnknownBruh 3 months ago
16 July Hamster Kombat Daily Cipher Code || Hamster Kombat Daily Cipher Code Today #dailychipercode #16july ...

MR Writer Saraiki. 3 months ago
today sipher code today cipher code today cipher code 21 june today cipher code hamster 23 june today cipher code hamster ...

Danny Nguyen 2 months ago
Resources I used to solve this machine: 1) The full guide that helped me solve the machine ...
Devslopes A year ago

Cryptos Univers 4 months ago
Venez découvrir dans ce tutoriel comment déverrouiller les #combo #cards de Hamster Kombat pour quotidiennement et ...

David Oranchak 3 years ago
This is a talk I gave in 2019 at the NSA's Cryptologic History Symposium, a little over a year before we discovered the solution to ...

Cyber Bangla 3 years ago
Home Work: Link: https://drive.google.com/file/d/1d7UNdgKJT77C6U98cRjYsDHA7-RsXqzt/view?usp=sharing ...

dtommy1979 14 years ago

BlueMonkey 4n6 A year ago
Magnet User Summit - Capture The Flag - May 2023 - Cipher ♥️ SUBSCRIBE for more videos: ...

BlueMonkey 4n6 2 years ago
Magnet Virtual Summit Capture The Flag 2023 - Cipher ♥️ SUBSCRIBE for more videos: ...

DragonChef91 4 months ago
Minecraft Find the Chomiks update 2.0 Use this for decoding challenging codes. It might have a cipher identifier but you still need ...

Junhua Wong 8 months ago
1. Encoding identifier online: https://www.dcode.fr/cipher-identifier 2. Vigenere cipher decryption ...

Tobi The Great 5 years ago
EDIT: I address the wrongs of this video here: https://youtu.be/h_EpXbRFDRs. In this video, I'll show you a few examples of ...

FuRy_ Gaming 4 years ago
Writeup for the challenge "Alice In Wonder Land" from NullBr3aker CTF2020. Cipher Identifier: ...

Knowledge Amplifier 2 years ago
This video is part of System Design playlist which explains how to create a pipeline which can be used for De-identification and ...

Cisco Secure Web Appliance 6 years ago
A brief illustration of the Server Name Indication extension to TLS and why it was added.

Crypto Quebec 19 days ago
Découvrez les secrets du succès commercial avec Market Cipher, l'indicateur essentiel dont tout trader a besoin en 2024 !

Code to the Moon 2 years ago
A quick tour of the Helix text editor / development environment, which is written in Rust. It's very similar to vim, but removes a ...

Cryptography for Everybody 3 months ago
cryptology, #cryptography, #cryptanalysis In this video, I present how we used artificial neural networks to break the Hagelin ...

SCCI Labs IIT Ropar 6 years ago

FuRy_ Gaming 4 years ago
Writeup for the challenge "SUBSTITUTE TEACHER" from NullBr3aker CTF2020. decoder: ...
![How to Myth Hunt [Tips for hunters, youtubers and more!]](https://i.ytimg.com/vi/TD14ReoNVSw/hqdefault.jpg)
Stalzie 6 months ago
゚☆✶⇣Open me⇣☆✶゚・. This video is a remake of my How to be a professional myth hunter". This is basically a part 2 and a lot ...

Leet Cipher 7 months ago
in this video, we go through the process of malware development in real life. we'll talk about various concepts such as shellcode, ...
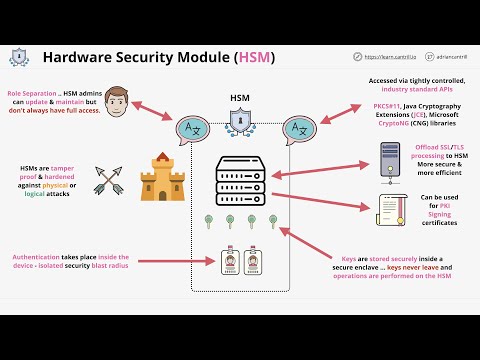
LearnCantrill 2 years ago
A Hardware Security Module (HSM) is a core part of the security posture of many organizations. It's a dedicated piece of hardware ...

Don't Panic Geocacher 3 years ago
This episode is part of an educational series that describe a structural approach that can help you solve mystery geocaches.

Retool 3 years ago
An overview of a free web tool for encoding and decoding Base64 strings / text. You can find this tool at: https://retool.com/utilities.

Ed Clark 5 years ago
Caesar's Cipher Named after Julius Caesar, Caesar's Cipher is one of the earliest known and simplest ciphers. It is a type of ...

Hackers GB 3 months ago
What is cryptography? Types of cryptography Cryptography tools Cryptography Tools Link: ...

Computerphile 5 years ago
Password1 is a terrible password, but how can I remember different secure passwords for each login? Use a password manager.

Naveen Chandra Gowda 4 years ago

Simons Institute 4 years ago
David Wu (University of Virginia) Lattices: Algorithms, Complexity, and Cryptography Seminar, Apr. 23, 2020 A software ...

SoBatistaCyber 5 months ago
Hello everyone! Welcome back to my channel! In this video, I'm excited to walk you through the solutions to 5 challenging picoCTF ...

ADiisolution 3 months ago
Pearson Edexcel Computer Science(4CP0) Lecture # 19( Encryption, Introduction,PigPen Cipher) for previous lectures link is ...